In the following entries we will be analyzing and implementing a few configurations in the Oracle SBCs that will enhance the security, but before we start working on that lets focus on some simple scenarios that will be used to test those security configurations.
Previously in Oracle SBC – Admin tasks – Basic load testing using SIPp we installed the software and create the most basic scenario generating traffic from the same source in the UAC to a unique destination in the UAS.
In the following scenarios we will keep the configuration in the UAS (this piece running in the server side is in charge of receiving the SIP requests and generate responses to those requests, which works fine with the default script) but we will make a few changes in the UAC (the element that generates the traffic, if needed please refer to the Basic load testing using SIPp entry) using CSV files.
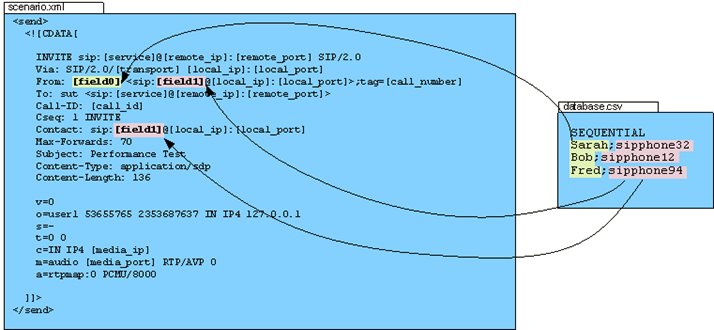
SIPp let you perform changes to the SIP signaling using XML files, which provides the ability to overwrite information from a CSV file into the SIP messages, the following image is a graphical representation of the use of a CSV file called database.csv to inject information in an specific XML scenario:
Will not take a deep dive into this, please refer to the following page to have a better understanding:
https://sipp.readthedocs.io/en/v3.6.1/scenarios/inject_from_csv.html
The purpose of this entry is create 2 scenarios and test them using the management interface, here are the description of the scenarios:
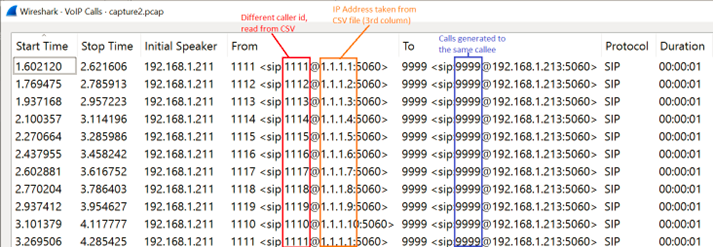
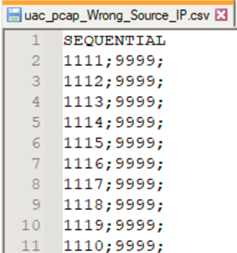
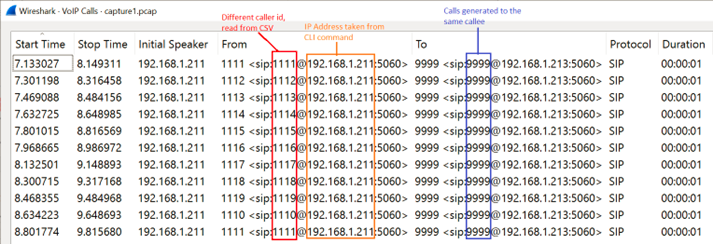
- Generating calls from different callers to the same callee (IP address will be taken by the UAC from the command line when running SIPp to generate calls), but we will use a CSV file called uac_pcap_Wrong_Source_IP.csv, this will help to generate calls from 10 different sources (1111 thru 1110) to an specific service (9999), this is a graphical representation (we will take a look in the specific xml files for each scenario):

2. Generating calls from different callers using different IPs to the same callee (this is an extension of the previous scenario but now spoofing the IP address in the signaling)

Now let’s go in details for the files used for each scenario previously described:
Scenario 1:
uac_pcap_Wrong_Source_IP.csv, the first column will represent the caller id to be used for the traffic generated, and the second column is the callee number or service running in the UAS. The following is how looks the XML scenario in the UAC, as previously mentioned field 0 = caller and field1 = called numbers
uac_pcap_Wrong_Source_IP.xml, describe the SIP messages that will be generated when running the UAC, field0 = caller and field1 = called numbers
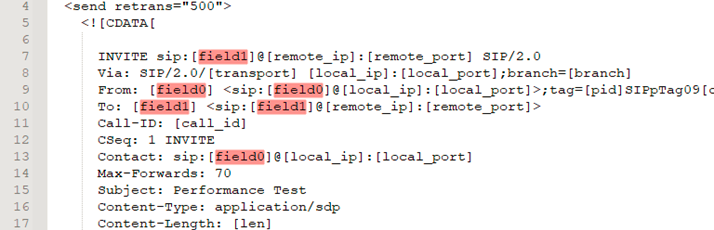
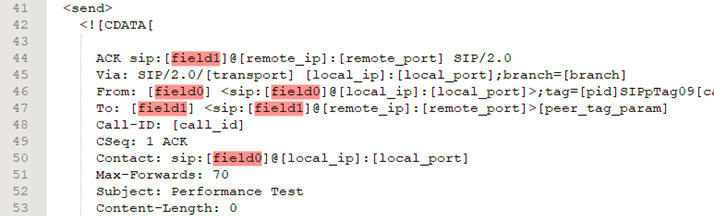
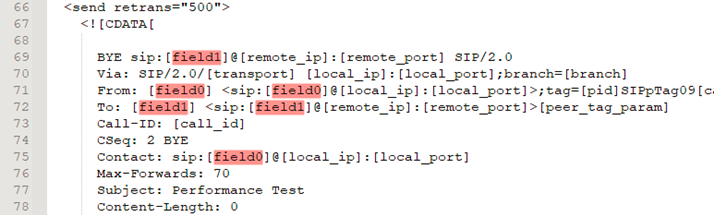
Now lets run a quick test and validate the scenario with the following commands:
UAC (call rate of 6, every 1 second until 200 calls are generated using interface 192.168.1.211 to 192.168.1.213 using port 5060):
sipp -sf uac_pcap_Wrong_Source_IP.xml -inf uac_pcap_Wrong_Source_IP.csv -r 6 -rp 1000 -m 200 -i 192.168.1.211 192.168.1.213 -p 5060 -trace_err
UAS (server running in interface 192.168.1.213):
sipp -sn uas -i 192.168.1.213 -m 200
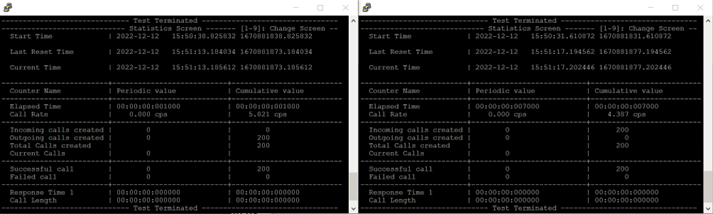
Here are the results:
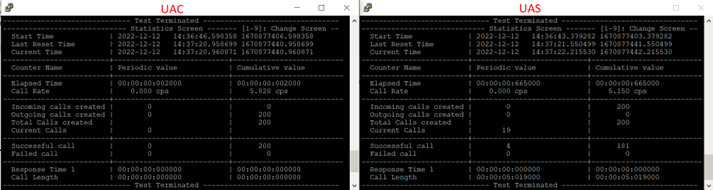
Scenario 2:
For this scenario, we will reuse the same CSV file but adding the spoofing IP address in the last column (it represents field2 in the XML)
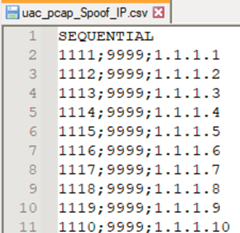
We will use the same previous xml file, only making the change for local_ip to field2
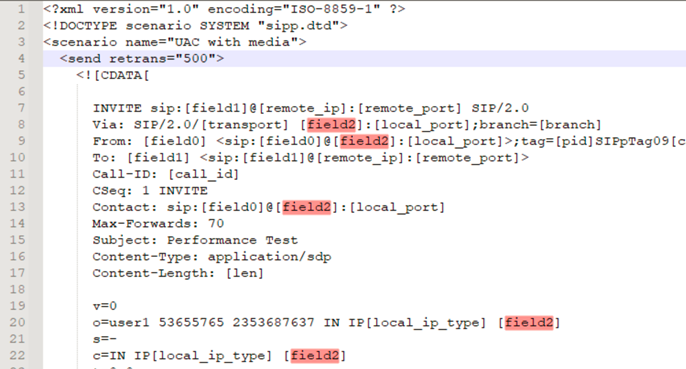
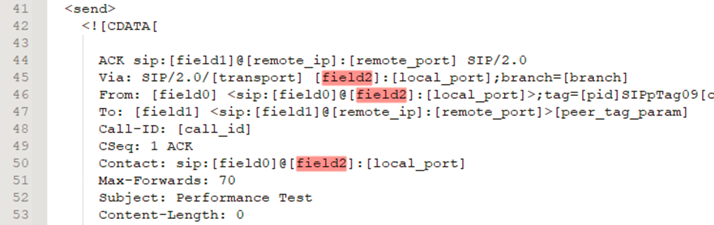
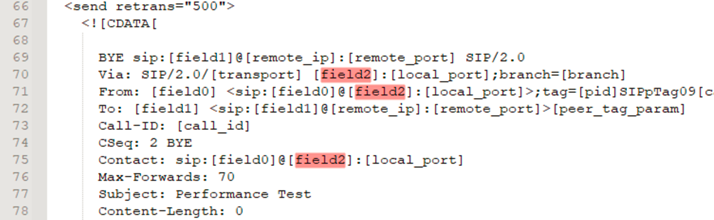
Lets validate this scenario the scenario with the following commands:
UAC (call rate of 6, every 1 second until 200 calls are generated using interface 192.168.1.211 to 192.168.1.213 using port 5060):
sipp -sf uac_pcap_Spoof_IP.xml -inf uac_pcap_Spoof_IP.csv -r 6 -rp 1000 -m 200 -i 192.168.1.211 192.168.1.213 -p 5060 -trace_err
UAS (server running in interface 192.168.1.213):
sipp -sn uas -i 192.168.1.213 -m 200
Here are the results: